Contact WebRAY
Tackling Cyber Risks in Healthcare: WebRAY Unveils Triple-Shield Solution at DMHC
Publication date:2025/08/27

From 22 to 24 August 2025, the Digital Medicine and Health Conference (DMHC) and the Hospital Construction and Design Expo (HCDE) were held at the Nanjing International Expo Center. At the event, WebRAY unveiled a triple-shield solution for healthcare institutions, inclduing the cyberspace asset security governance, commercial cryptography application development, and API security governance. It also presented a specialized self-inspection tool targeting “Two Highs, One Weak” compliance check (high-risk vulnerabilities, high-risk ports, and weak passwords).
Drawing on its extensive technical expertise and practical experience, WebRAY delivered a comprehensive analysis of industry challenges and mitigation strategies, which garnered considerable attention from experts and industry peers.
In recent years, as the healthcare industry has been advancing its digital transformation, the network security challenges it faces have become increasingly severe. Healthcare systems now commonly suffer from inadequate implementation of China's Cybersecurity Classified Protection System, weak protection framework, frequent ransomware attacks, and high incidence of data breaches. According to IBM's 2024 Cost of a Data Breach Report, the average cost of a data breach in the healthcare industry has reached $9.77 million, making it the most costly industry globally for the 14th consecutive year. Consequently, healthcare institutions urgently need to establish systematic security capabilities that ensure “real-time detection, tiered response, and compliance-driven closure.”
Against this backdrop, WebRAY, with its "triple-shield" solution and "15-minute self-inspection tool", offers a one-stop, zero-transformation, and implementable new paradigm for security governance to support the digital transformation of hospitals.
Cyberspace Asset Security Governance Solution for Healthcare Institutions
This solution aims to implement comprehensive and detailed management of all IT assets within the hospital. It ensures precise control over all assets in the hospital network through five key steps: rapid scanning, accurate identification, registration and labeling, threat correlation, and closed-loop handling.
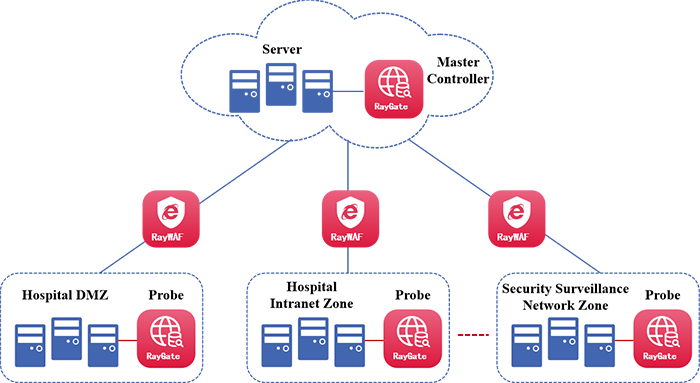
Commercial Cryptography Application Solution for Healthcare Institutions
- Fortify Data Security and Privacy Protection
The solution employs compliant cryptographic techniques to encrypt sensitive data such as patient identity information, electronic medical records, and diagnostic results. It ensures the confidentiality, integrity, and availability of data during transmission and storage, effectively preventing data breach and tampering at the source.
- Strengthen Identity Authentication and Trusted Access Mechanisms
Leveraging commercial cryptographic technologies, the identities of professionals, patients, and hospital information systems can be precisely verified. It ensures that only authorized users can access and operate the telemedicine system, effectively preventing impersonation attempts. This provides a trusted foundation for the secure flow of medical resources and services, thereby enhancing the quality and security of healthcare services.
- Ensure Compliant Operation and Sustainable Development
The solution fully aligns with China's laws and regulations, including Cybersecurity Law, and Administrative Measures for the Security Assessment of Commercial Cryptography Application, mitigating legal risks and regulatory penalties through standardized cryptography applications. It establishes a solid compliance foundation for the long-term stable operation of telemedicine systems, empowering the sustainable development of the healthcare industry.
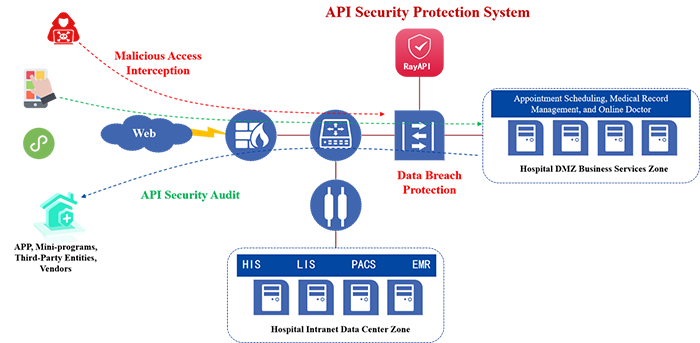
API Security Governance Solution for Healthcare Institutions
Starting with API asset management, the solution has covered various stages, including API discovery, classification profiling, attack protection, and access control. It automatically organizes various business API interfaces within the hospital through traffic learning and creates multi-dimensional API asset profiles by considering system attributes, business types, and organization structures. Based on this, it monitors, alerts and addresses risks like unauthorized data exposure, sudden spikes in data access, and illegal interface access. Additionally, by integrating threat intelligence and database security auditing capabilities, the solution ensures full lifecycle coverage, empowering users to make cybersecurity risks known, manageable, and controllable.
Self-Inspection Tool for "Two Highs, One Weak" for Healthcare Institutions
In response to regulatory agencies' "Two Highs, One Weak" compliance check for healthcare institutions, WebRAY has launched a dedicated self-inspection tool. Utilizing non-intrusive scanning technology, this tool is equipped with a database that includes over 1,400 items specified by regulatory requirements under the "Two Highs, One Weak" category, as well as an extended library tailored for the healthcare industry. It performs a comprehensive scan of core systems, web applications, databases, and network devices within 15 minutes, and provides a remediation plan tailored to the user's current situation.
About RayWAF
- Intelligent Protection Redefined | RayWAF
Leveraging 15+ years of cybersecurity expertise, WebRay's RayWAF delivers enterprise-grade protection through adaptive, AI-powered defense. This multi-layered solution combines behavioral analysis, machine learning, and real-time threat prevention to effectively combat both known vulnerabilities and emerging threats—including zero-day exploits and business logic attacks—while ensuring optimal performance across cloud, hybrid, and on-premises environments.
- Intelligent Semantic Protection
ML-driven semantic analysis for context-aware threat blocking with near-zero false positives
- Machine Learning Protection
Real-time ML profiling of site behavior with adaptive threat detection (99.99% accuracy).
- Scan Trap Protection
Decoy-based anti-crawler defense against bots and path traversal attacks.
- Honeypot Dual-Mode Threat Protection
Honeypot-powered active-passive defense with attack detection and source tracing.
- BOT Protection
Patented dynamic token authentication approach prevents automated attacks and transaction fraud.
- Active Defense via Bypass Mirroring
Bypass deployment mode ensures business with uninterrupted security for mission-critical systems.